The internet is much bigger than what we see every day. When you search on Google, scroll through Facebook, or visit your favorite websites, you’re only exploring the surface web, a small portion of the entire internet.
Beneath that surface lies something deeper and less understood: the Dark Web. It’s often surrounded by mystery, fear, and misconceptions. But what is it really, and how does it work? Let’s break it down in simple terms.
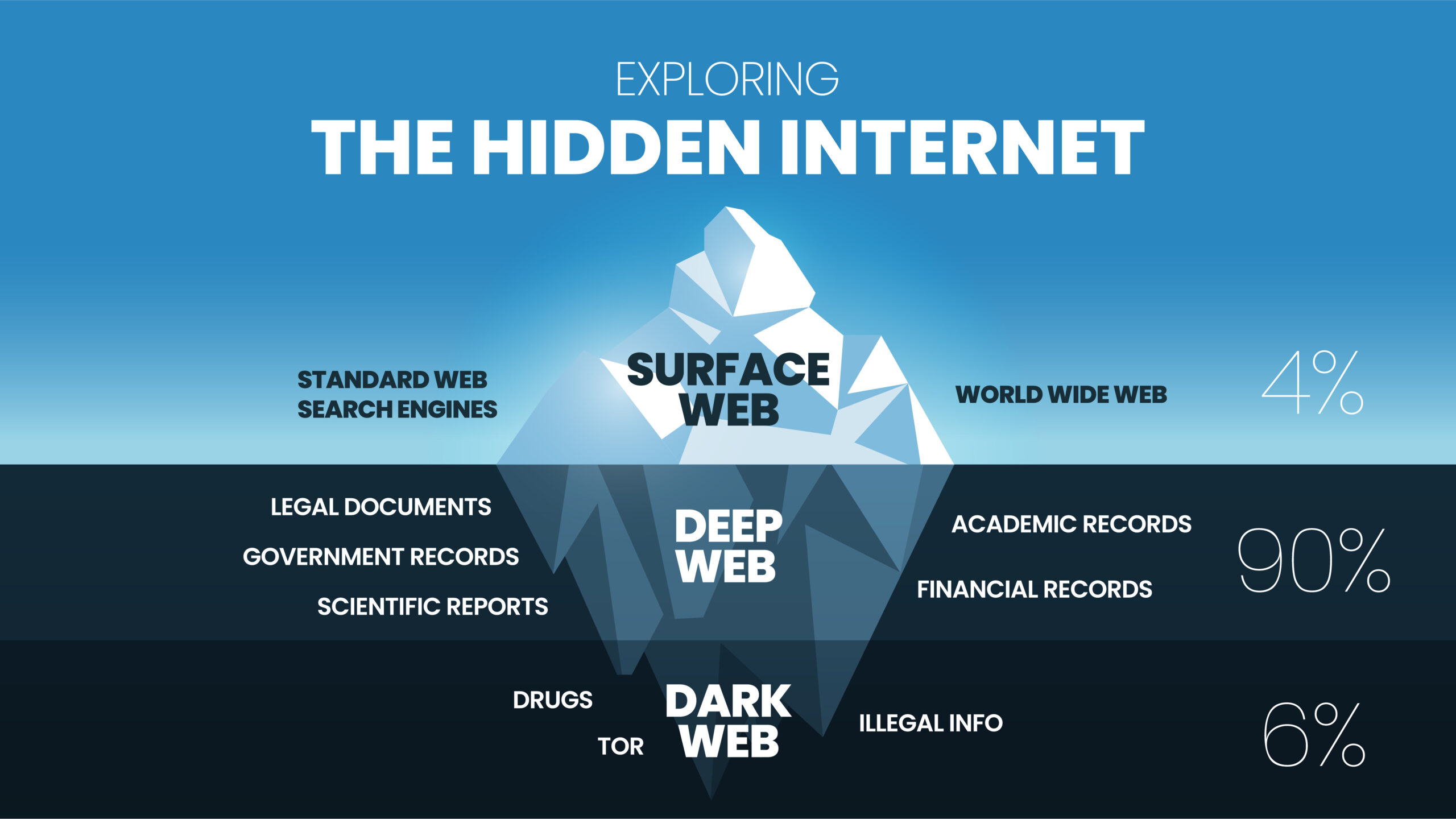
1. The Three Layers of the Internet
To understand the Dark Web, it helps to first know the three main parts of the internet:
a. Surface Web
This is the part of the internet that’s publicly accessible and indexed by search engines like Google, Bing, or Yahoo. Examples include:
-
News sites (BBC, CNN)
-
Social media (Facebook, Instagram)
-
Online stores (Amazon, eBay)
Anyone can access the surface web using a regular browser such as Chrome or Safari.
b. Deep Web
This layer is not indexed by search engines, meaning it can’t be found through a Google search. However, it’s not illegal or mysterious.
The Deep Web includes:
-
Private email inboxes
-
Online banking dashboards
-
Cloud storage and academic databases
-
Corporate or government intranets
Basically, any page that requires a login or special permission sits in the Deep Web.
c. Dark Web
The Dark Web is a small part of the Deep Web that has been intentionally hidden. It cannot be accessed through regular browsers. Instead, it requires special software such as Tor (The Onion Router) or I2P to access.
This is where anonymity and privacy take center stage.
2. How the Dark Web Works
The Dark Web operates on encrypted networks that hide users’ identities and locations. When you connect through Tor, your data is routed through multiple servers around the world, bouncing from one to another like a secret relay race.
This process:
-
Encrypts your internet traffic multiple times
-
Masks your IP address (so no one can see your real location)
-
Prevents easy tracking of your online activity
In simpler terms, the Dark Web provides anonymity. This is both its biggest strength and its biggest weakness.
3. What’s on the Dark Web?
Contrary to popular belief, not everything on the Dark Web is criminal. It hosts both legal and illegal activities. Here are some examples:
Legal Uses:
-
Whistleblowing platforms: Journalists and activists use it to share sensitive information securely (e.g., Wikileaks).
-
Privacy forums: Users who value digital privacy discuss cybersecurity, encryption, and free speech.
-
Secure communication: People living under oppressive governments use it to bypass censorship.
Illegal Uses:
-
Black markets: Sale of stolen data, drugs, counterfeit items, or weapons.
-
Hacking services: Offering malware, phishing tools, or stolen credit card information.
-
Identity theft: Buying or selling personal data such as bank credentials and social media accounts.
Because of these illegal markets, law enforcement agencies across the world constantly monitor Dark Web activity.
4. Advantages of the Dark Web
Despite its dark reputation, there are legitimate benefits to this hidden part of the internet:
a. Privacy and Anonymity
The Dark Web protects users from surveillance and censorship. Journalists, human rights workers, and researchers use it to communicate safely in regions where freedom of speech is restricted.
b. Freedom of Information
It allows people in countries with heavy internet censorship to access global news, share opinions, and publish reports anonymously.
c. Security Research
Cybersecurity professionals use the Dark Web to study hacking trends, analyze threats, and prevent future cyberattacks.
5. Limitations and Dangers of the Dark Web
While there are benefits, the Dark Web also comes with serious risks:
a. Illegal Content
Many sites host illegal material, something that can lead to severe legal consequences just by visiting or downloading the wrong content.
b. Cyber Threats
Scams, phishing, and malware are common. Without strong security measures, users can easily get hacked or have personal data stolen.
c. No Guarantees of Anonymity
Even though Tor hides your identity, no system is 100% secure. Governments and cybersecurity experts have successfully tracked illegal activities on the Dark Web.
d. Ethical and Legal Concerns
Some activities that seem harmless could still violate local or international laws. Understanding where to draw the line is crucial.
6. Should You Use the Dark Web?
For most regular internet users, there’s no need to access the Dark Web. The Surface Web and Deep Web already provide everything you need, secure banking, research, entertainment, and communication.
However, for those working in cybersecurity, journalism, or privacy advocacy, the Dark Web can be a valuable tool if used responsibly.
If you ever explore it:
-
Use a VPN and the Tor browser.
-
Avoid sharing personal information.
-
Never download files from unverified sources.
-
Stay aware of local and international laws.
7. Final Thoughts
The Dark Web is not entirely “evil.” It’s simply a part of the internet designed for anonymity. Like any powerful tool, it can be used for both good and bad.
It offers privacy, freedom, and secure communication but it also harbors illegal trade, cybercrime, and danger.
Understanding how it works helps demystify it and reminds us that the real challenge lies not in the technology itself, but in how people choose to use it.

Leave a Reply